 Hack Remote P.C. using latest java vulnerability
Hack Remote P.C. using latest java vulnerability
JAVA APPLET JMX REMOTE CODE EXECUTION:- This vulnerability is exploited in February 2013. Additionally, this module bypasses def...
Leading source of Information Security, Hacking News, Cyber Security, Network Security with in-depth technical coverage of issues and events
 Hack Remote P.C. using latest java vulnerability
Hack Remote P.C. using latest java vulnerability
JAVA APPLET JMX REMOTE CODE EXECUTION:- This vulnerability is exploited in February 2013. Additionally, this module bypasses def...
Today, I would tell you step by step on how you can setup your own botnet and start playing with it, Botnet could be used to perform wide ...
 Anonymous Hacks Bank Of America
Anonymous Hacks Bank Of America
Anonymous has gained a lot of stardom (good and bad) by crashing websites and hacking government servers. Anonymous usually come in handy wh...
 How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
Apple has been a bit bitter past a few of its iOS releases making it that much easier for iOS device users to spit out what they chew. After...
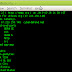 Use NMAP as a Information gathering tool
Use NMAP as a Information gathering tool
Usually we use NMAP as a port scanner to find open port of web-server, But with help of this Tool we can also gather Information about vict...
 How to Bypassing Filter to Traversal Attacks ?
How to Bypassing Filter to Traversal Attacks ?
Bypassing Filter to Traversal Attacks If your initial attempts to perform a traversal attack, as described previously, are unsuccessful, thi...
 DOM Based XSS In AVG
DOM Based XSS In AVG
Lately, i have been researching on DOM based XSS a bit, Recently i found a DOM based XSS in AVG, DOM based XSS is caused due to lack of inpu...