 How To Crack A WPA Key With Aircrack-ng
How To Crack A WPA Key With Aircrack-ng
With the increase in popularity of wireless networks and mobile computing, an overall understanding of common security issues has become not...
Leading source of Information Security, Hacking News, Cyber Security, Network Security with in-depth technical coverage of issues and events
 How To Crack A WPA Key With Aircrack-ng
How To Crack A WPA Key With Aircrack-ng
With the increase in popularity of wireless networks and mobile computing, an overall understanding of common security issues has become not...
 Java Hits Another Roadblock - Found To Be A Threat For Browsers
Java Hits Another Roadblock - Found To Be A Threat For Browsers
Java has been the most talked about application in the past couple of months. Not because of its functionality but due to its inability to r...
 ASP.NET web-application Testing
ASP.NET web-application Testing
Lens is an open-source ethical hacking tool specialized to penetration testing of ASP.NET web applications. Lens is written in WPF 4 and its...
 DOM Based XSS In Microsoft
DOM Based XSS In Microsoft
Lately, i have been researching on DOM based XSS a bit, In my previous post i talked about the DOM based XSS i found inside AVG ...
 How Attackers Spread Malware With Java Drive by?
How Attackers Spread Malware With Java Drive by?
Hello RHA fans, We are back with a new tutorial. Well making a malicious virus is one thing but how to spread it? Or how hackers hunt for v...
 Web-application Fingerprinting
Web-application Fingerprinting
Methods of Web Application Finger Printing Historically Identification of Open Source applications have been easier as the behavior pattern ...
 Cisco ZeroClipboard Swf File XSS
Cisco ZeroClipboard Swf File XSS
The security of the target website depends upon the number of vectors an attacker knows, The more vectors an attacker knows the more chance...
 Vulnerability Discovered In iPhone - Poses Serious Threat To Users
Vulnerability Discovered In iPhone - Poses Serious Threat To Users
Another vulnerability has been discovered on iPhone that could allow hackers to remotely control it. Skycure, an Israeli company, states it ...
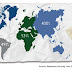 600% Increase In Cyber Attacks: WebSense Releases Threat Report 2013
600% Increase In Cyber Attacks: WebSense Releases Threat Report 2013
One thing I love more than writing is online threat reports - all the blood, sweat and tears combined with the satisfaction of discovery and...
 Vulnerabilities Fixed in App Store Almost After A Year
Vulnerabilities Fixed in App Store Almost After A Year
It is being reported that Apple has ignored its network's security for more than a year. A problem that a Google developer has pointed ...
 How To Dodge Android 4.1.2 Passcode Lock - Vulnerability Exploited And Explained
How To Dodge Android 4.1.2 Passcode Lock - Vulnerability Exploited And Explained
Do you want to elude Note II's security even for a brief moment? With iOS 6.1.2 being owned by hackers , it was time that someone took a...
 Microsoft Word UNC Path Injector
Microsoft Word UNC Path Injector
This module modifies a .docx file that will, upon opening, submit stored netNTLM credentials to a remote host. It can also create an empty d...
 The Rise Of Ethical Hackers - Let The Bounty Hunting Begin!
The Rise Of Ethical Hackers - Let The Bounty Hunting Begin!
Well, well well! It seems like our own favourite ethical hacker, Rafay Baloch , is about to meet the clan with whom he shares his talents! ...
 Java Zero-Day Vulnerabilities Fixed By Oracle
Java Zero-Day Vulnerabilities Fixed By Oracle
We recently reported two Java zero-day vulnerabilities that were spotted in the wild by FireEye now identified as the CVE-2013-1493 and CV...
.jpg) MySQL Injection Time Based
MySQL Injection Time Based
We have already written a couple of posts on SQL Injection techniques, Such as " SQL Injection Union Based ", " Blind SQL Inj...
![How Hackers Make Botnets To Infect Systems [Part 2]](http://1.bp.blogspot.com/-htG7vy9vIAA/Tp0KrMUdoWI/AAAAAAAABAU/e7XkFtErqsU/s1600/grey.gif) How Hackers Make Botnets To Infect Systems [Part 2]
How Hackers Make Botnets To Infect Systems [Part 2]
Hello RHA readers, we are back with How To Setup A Botnet [Tutorial For Noobs] [Part 2]. Those who haven't read previous part than check...
 Another Java Zero-Day Vulnerability Spotted In The Wild
Another Java Zero-Day Vulnerability Spotted In The Wild
So, you thought you were out of the woods with Java? Bad news. You aren't. Another Java zero-day vulnerability has been found in the wil...
Introduction Cross Site Scripting or XSS vulnerabilities have been reported and exploited since 1990s. XSS got listed as the top 3 rd Vulne...