 How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
Apple has been a bit bitter past a few of its iOS releases making it that much easier for iOS device users to spit out what they chew. After...
Leading source of Information Security, Hacking News, Cyber Security, Network Security with in-depth technical coverage of issues and events
 How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
How To Dodge iOS 6.1.2 Passcode - Vulnerability Exploited And Explained
Apple has been a bit bitter past a few of its iOS releases making it that much easier for iOS device users to spit out what they chew. After...
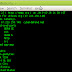 Use NMAP as a Information gathering tool
Use NMAP as a Information gathering tool
Usually we use NMAP as a port scanner to find open port of web-server, But with help of this Tool we can also gather Information about vict...
 How to Bypassing Filter to Traversal Attacks ?
How to Bypassing Filter to Traversal Attacks ?
Bypassing Filter to Traversal Attacks If your initial attempts to perform a traversal attack, as described previously, are unsuccessful, thi...
 DOM Based XSS In AVG
DOM Based XSS In AVG
Lately, i have been researching on DOM based XSS a bit, Recently i found a DOM based XSS in AVG, DOM based XSS is caused due to lack of inpu...
 Path traversal vulnerabilities Tutorial
Path traversal vulnerabilities Tutorial
Path traversal vulnerabilities arise when user-controllable data is used by the application to access files and directories on the applicati...
 Adobe Zero Day Malware - Upgrade Adobe Reader and Acrobat
Adobe Zero Day Malware - Upgrade Adobe Reader and Acrobat
A few days ago we blogged about Adobe's Zero-Day Malware affecting Adobe Reader and Acrobat. The malware was investigated on by Sophos ...
 All Problems And Solutions Related To SQL injection
All Problems And Solutions Related To SQL injection
Today I'll write a tutorial for you that covers most problems while applying SQL injection and solutions t...
 Jailbreak iOS 6.1.2 Untethered On All iDevices
Jailbreak iOS 6.1.2 Untethered On All iDevices
Apple has been quick to patch the last of the bugs found in the iOS 6.1.1. With the release of iOS 6.1.2 it seemed that Apple would patch th...
 BlackBerry Users At Risk
BlackBerry Users At Risk
Attention all BlackBerry users! You are vulnerable to remote attacks by hackers. It has been reported by Blackberry security advisory that i...
 Facebook's Security Breeched - Java Zero-Day Vulnerability Found
Facebook's Security Breeched - Java Zero-Day Vulnerability Found
Facebook was attacked by unidentified hackers on Friday. The attack was carried out when Facebook Co.'s employees visited a developer...
.jpg) Blind SQL Injection - Detection And Exploitation
Blind SQL Injection - Detection And Exploitation
In our previous post " SQL Injection Basics - Union Based ", I explained the basic technique not only to find detect sql injection...
 OWASP TOP 10 Security RISKS For 2013
OWASP TOP 10 Security RISKS For 2013
The OWASP or the Open Web Application Security Project's " top 10 " has been designed to raise awareness about crucial securi...
 Adobe Zero Day - How To Protect Yourselves?
Adobe Zero Day - How To Protect Yourselves?
A couple of hours ago, we wrote a detailed blog on Adobe's Zero-Day malware, found by Fireeye and investigated by Sophos Lab. The malwa...